soc 2 physical security|Simplify SOC 2 compliance with the right physical : Bacolod SOC 2 controls encompass a comprehensive set of measures derived from SOC 2 Trust Services Criteria that an auditor evaluates while creating a SOC 2 report. Some examples of SOC 2 controls include . Convert your Rewards Points into RCBC Credit Card AIRMILES which you can redeem for your choice of mileage points: Mabuhay Miles (Philippine Airlines), Asia Miles (Cathay Pacific), or airasia points. There are no limits on how many RCBC Credit Card AIRMILES you can earn and they never expire!. You can redeem your RCBC Credit Card .
PH0 · What Is SOC 2 Compliance?
PH1 · The Ultimate SOC 2 Controls List
PH2 · Simplify SOC 2 compliance with the right physical
PH3 · SOC 2 Policies and Procedures
PH4 · SOC 2 Physical Security Requirements: Meaninga
PH5 · SOC 2 Physical Security Requirements
PH6 · SOC 2 Controls List
PH7 · SOC 2 Academy: Physical Security Controls
PH8 · 12 Commonly Recommended Security Policies for SOC 2
Ang saklaw ng pag-aaral ng heograpiya ay may dalawang kategorya, ito ang Pisikal na Heograpiya (Physical Geography) at ang Heograpiyang Pantao (Human Geography). Pisikal na Heograpiya . Nakatuon ang pag-aaral sa likas na kapaligiran ng mundo pati na rin sa pisikal na katangian nito. Saklaw nito ang mga anyong lupa at .
soc 2 physical security*******SOC 2 physical security requirements encompass the policies, procedures, and controls designed to protect an organization’s physical assets and sensitive information. These requirements focus on preventing unauthorized access, .
SOC 2 Policies. All SOC 2 examinations involve an auditor review of your organization’s policies. Policies must be documented, formally reviewed, and accepted by employees. Each policy .
SOC 2 requires that measures are taken to protect the physical access to the organization’s systems and facilities. Physical security is specifically addressed in CC6.4 of the AICPA’s .How to Prepare for an Audit. Define Your SOC 2 Audit Scope. SOC 2 Compliance Requirements. Establishing a SOC 2 Project Plan. SOC 2 Policies and Procedures. SOC 2 Compliance .soc 2 physical security SOC 2 controls encompass a comprehensive set of measures derived from SOC 2 Trust Services Criteria that an auditor evaluates while creating a SOC 2 report. Some examples of SOC 2 controls include . What is a SOC 2 Policy? What Policies Do I Need to Have in Place? What Policies Are Included in Drata? Commonly Asked Questions About SOC 2 Policies. Providing your .
SOC 2 (System and Organization Controls) is an auditing framework developed by the American Institute of Certified Public Accountants (AICPA) that assesses an organization's controls .Simplify SOC 2 compliance with the right physical SOC 2 Type II accreditation provides peace of mind that proper procedures are in place to ensure data stored within the Genetec system is secure, private and confidential. It also provides independent validation that . Like. 1.6K views 5 years ago SOC 2 Academy. Learn more at https://kirkpatrickprice.com/video/so. While malicious hackers often attack digitally, organizations must account for the. Use our SOC 2 audit checklist if you’re using Amazon’s AWS cloud services and need to become SOC 2 compliant each year. . First, a large number of the physical security controls are covered by AWS themselves as their private data centers store your virtual server instances. Second, AWS has a fair number of audit & compliance, and control .
The first is the duration of time in which the controls are evaluated. A SOC 2 Type 1 audit looks at controls at a single point in time. A SOC 2 Type 2 audit looks at controls over a period of time, usually between 3 and 12 months. .
Continuous, around-the-clock security monitoring: The SOC monitors the entire extended IT infrastructure—applications, servers, system software, computing devices, cloud workloads, the network—24/7/365 for signs of known exploits and for any suspicious activity. For many SOCs, the core monitoring, detection and response technology has been security information and .SOC 2 (service organization controls) ISO 9001 (quality management) ISO 27001 (information security) PCI-DSS (AoC) . with an integrated multi-layered physical and logical security approach that is both responsive to customer requirements and meets the most stringent internationally recognized third party certifications.SOC 2 is a standard for information security based on the Trust Services Criteria. It’s open to any service provider and is the one most commonly requested by potential customers. SOC 3 is also based on the TSC but is less thorough, with results that can be shared publicly. . Logical and physical access controls: .
What is SOC 2 Logical and Physical Access (CC6)? . Encrypt your data in transit and do so with secure protocols (this means TLS 1.2 or TLS 1.3 these days). Protects Removable Media – For removable media used to send data over the sneakernet, such as USB drives, tape drives, ZIP drives, or 5.25″ floppy drives, have appropriate controls .
soc 2 physical security Simplify SOC 2 compliance with the right physical The TSC is unlike other regulatory compliance frameworks in that it does not prescribe a SOC 2 security controls list that companies need to implement. Instead, . SOC 2 Logical and Physical Access Controls. The first set of controls measured by the TSC pertains to logical and physical access. These controls include safeguards to monitor and .
Nevertheless, the significance of the role of SOC 2 in data security cannot be underestimated. Understanding its origins can help to explain why. History of SOC 2. SOC 2 evolved from the Statement on Auditing Standards (SAS) 70, an old audit that Certified Public Accountants (CPAs) used to assess the effectiveness of an organization’s .AWS data centers are secure by design and our controls make that possible. Before we build a data center, we spend countless hours considering potential threats and designing, implementing, and testing controls to ensure the systems, technology, and people we deploy counteract risk. . AWS provides physical data center access only to approved .

What is SOC 2 Logical and Physical Access (CC6)? Organizations are responsible for controlling logical and physical access to their protected information by using appropriate security software, infrastructure, and architectures. Implementing and maintaining these necessary controls will protect your company’s valuable data and prevent unwanted .
SOC 2 stands for Systems and Organization Controls 2. It was created by the AICPA in 2010. SOC 2 was designed to provide auditors with guidance for evaluating the operating effectiveness of an organization’s security protocols. The SOC 2 security framework covers how companies should handle customer data that’s stored in the cloud.AICPA Trust Services Criteria define five criteria for evaluating an organization’s security controls for SOC 2 compliance: security, availability, processing integrity, confidentiality, and privacy. . CC6 – Logical and Physical Access Controls Does the organization encrypt data? Does it control who can access data and restrict physical .
Evaluating SOC 2 Security Controls. Security refers to the protection of: Information during its collection, creation, use, processing, transmission, and storage. . (CC5) are further broken out into logical and . A.11: Physical and environmental security: April 8, 2024: SOC 1 (Azure) PE-1: Datacenter physical access provisioning PE-2: Datacenter security verification PE-3: Datacenter user access review PE-4: Datacenter physical access mechanisms PE-5: Datacenter physical surveillance monitoring PE-6: Datacenter critical environment maintenanceSecurity Management. 37(3), 1993. pp. 43-48. Miehl, F. "The Ins and Outs of Door Locks." Security Management. 37(2), 1993. pp. 48-53. National Bureau of Standards. Guidelines for ADP Physical Security and Risk Management. Federal Information Processing Standard Publication 31. .
When it comes to data security, the SOC 2 Trust Services Criteria (TSC) is one of the most critical standards. These standards cover everything from physical security to data encryption. There are five key categories in the TSC, listed below: Security. Security is defined as protecting databases and systems from unauthorized access .
Security: Evaluates whether your systems and controls can protect information against physical access, damage, use, or modifications that could hinder users. Security is also known as the “common criteria,” as it’s the only mandatory trust principle. . SOC 2 is a security framework, and SOC 2 compliance involves establishing security .
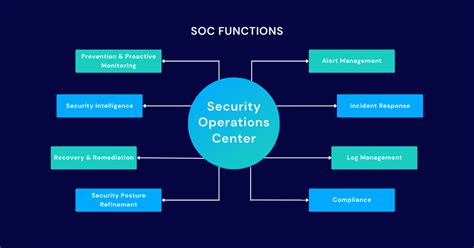
Many virtual SOCs use a combination of contract and full-time staff. An outsourced SOC, which also may be called a managed SOC or a security operations center as a service, is run by a managed security service provider, who takes responsibility for preventing, detecting, investigating, and responding to threats.
UK EuroMillions players can win a top prize of £1 million in the free Millionaire Maker Raffle, included in the tickets price when you play! Millionaire Maker Codes. Casino Games. Win huge jackpots instantly with these great casino game favourites! Dr Watts Up. Play Now. Hyper Gold. Play Now. Rainbow Riches. Play Now. Foxin' Wins.
soc 2 physical security|Simplify SOC 2 compliance with the right physical